In order to configure Compliance module you need to configure the followin components:
- Compliance Templates
- Compliance Rules
- Global Options
- Compliance Jobs
1. Compliance Templates
Compliance Template is a configuration object which maps interface commands to a Compliance Result. The commands configured on an interface are matched against commands specified by Compliance Templates. If all the commands are matched, the template result is assigned to the interface.
Templates can have the following results:
- Compliant - The interface is configured as expected, no action is needed.
- Partially Compliant - There are minor misconfigurations on the interface which have to be there for any reason, but you want to be aware of them e.q. Incorrect access VLAN, incorrect authentication priority, order, host mode, etc. You consider partially compliant interfaces as still secured.
- Non Compliant - The interface contains configurations which should not be configured. An action should be taken to configure the interface into Compliant state.
Commonly, there are multiple Compliant Templates in an organization. This can be due to different requirements based on a connected Endpoint to the interface, version of IOS, or a switch model. You should configure all of them.
Variables
Dynamic variables
The compliance template can have a few variables which dynamically assign the access and voice VLAN number to the template. The following code block gives you an example of how to configure the variables to access or voice command.
switchport access vlan {<vlan string>;<default value>}
switchport voice vlan {<vlan string>;<default value>}
For example:
switchport access vlan {ise_users;10}
switchport voice vlan {ise_voip;90}
The ise_users and ise_voip are the variables which are assigned based on the following rules:
Please note the the variable names are the actual string in a switch configuration, thus the name dynamic variables
- Search for a vlan group command in a switch configuration. The following command in our example will assign No. 10.
vlan group ise_users vlan-list 10
- Search for VLAN name in the VLAN configuration. The following configuration will assign No. 10
vlan 10
name ise_users
- Use the default value in the variable configuration.
When the access VLAN is determined, it is replaced in the Compliance Template. This occurs on a per switch bases, Every switch can have it's own access and voice VLANs. This allows you to match or configure access and voice VLAN individually per switch.
Static variables
Another variable which can be configured in a Compliance template is static "access_vlan" variable. The term "access_vlan" is a fixed variable name and it's value is derived from the command switchport access vlan <vlan>. This variable can be used in an interface description or in the command bellow. Static and Dynamic variables can be combined.
authentication event server dead authorize vlan {access_vlan}
description Access VLAN on this port is: {access_vlan}
This feature is very usefull if you do not push VLAN numbers dynamicaly from ISE but rather configure them statically. Access VLAN variable ensures that your critical VLAN configuration is always the same as access VLAN configuration.
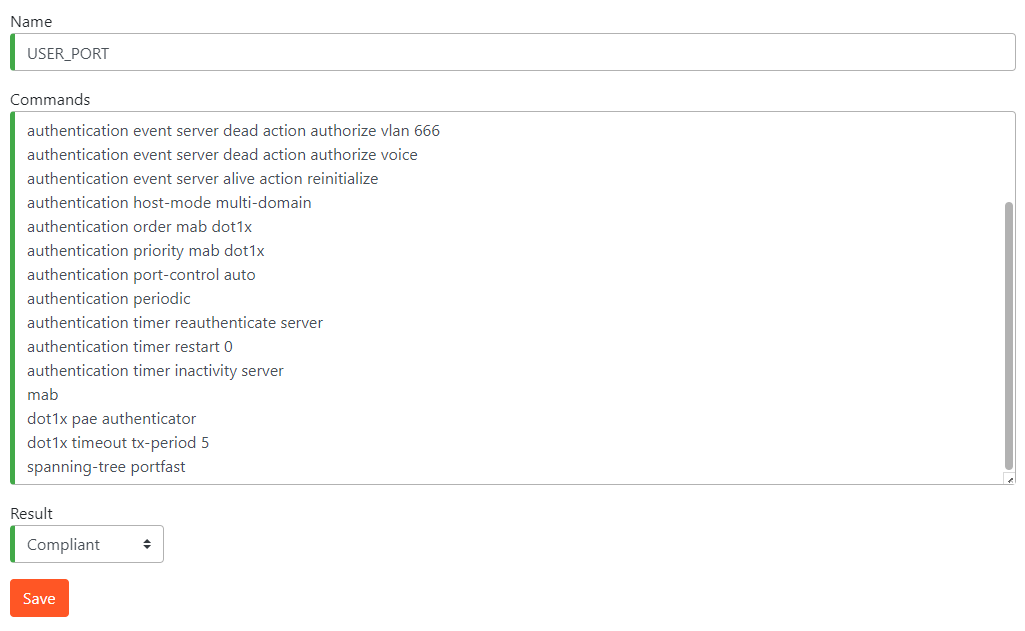
Compliant Template Example
The following Compliance Template shows you an example of a common compliant interface template configuration. A compliance template should contain all interface commands which should be configured a secured switch port in your network.
description >DOT1X<
switchport mode access
switchport access vlan {ise_users;10}
switchport voice vlan {ise_voip;120}
authentication host-mode multi-domain
authentication periodic
authentication timer reauthenticate server
authentication timer inactivity server dynamic
authentication event fail action next-method
authentication event server dead action reinitialize vlan 666
authentication event server dead action authorize voice
authentication event server alive action reinitialize
authentication control-direction in
authentication timer restart 0
authentication order mab dot1x
authentication priority mab dot1x
authentication port-control auto
authentication violation restrict
mab
dot1x pae authenticator
dot1x timeout tx-period 5
spanning-tree portfast
All the commands in a Compliance Template are compared to interface commands in the Exact Match manner except the description command, which is matched in the Starts with manner. This means that for example spanning-tree portfast command in a template will not match the spanning-tree portfast edge command on an interface.
- If there is a command missing on an interface, template will not match
- If there are more commands configured on an interface but all the commands in the template matched then the template matched and the Template Result is assigned to the interface
Partially Compliant Template Example
The following example shows you a configuration of a partially compliant template. Partially compliant template works the same as compliant template and should include all commands required on an interface. Partially compliant templates does not follow your configurations standards perfectly but you still consider these configurations as secure.
In this example, the template contains the command authentication host-mode multi-auth which may not be your desired configuration.
description >DOT1X-AP<
switchport mode access
switchport access vlan {ise_users;10}
switchport voice vlan {ise_voip;120}
authentication host-mode multi-auth
authentication periodic
authentication timer reauthenticate server
authentication timer inactivity server dynamic
authentication event fail action next-method
authentication event server dead action reinitialize vlan 666
authentication event server dead action authorize voice
authentication event server alive action reinitialize
authentication control-direction in
authentication timer restart 0
authentication order mab dot1x
authentication priority mab dot1x
authentication port-control auto
authentication violation restrict
mab
dot1x pae authenticator
dot1x timeout tx-period 5
spanning-tree portfast
Non Compliant Template Example
The following example shows you a configuration of a non compliant temlate. Template should contains a command or a selection of commands which must not be configured on an interface. Please note that if you specify more commands in a non compliant template, then all the commands must be configured on an interface in order the non compliant template to match.
authentication open
Configuration
- Navigate to Compliance Module -> Compliance Configuration (Page 1)
- Click on the New button
- Fill the name, Commands and select Result and click Save.
2. Compliance Rules
The next concept in Compliance configuration are Compliance Rules. The Compliance Rules determine which templates a switch will be evaluated to. In other words, which templates will be chosen for the switch.
The logic work in the same way as firewall rules. Compliance rules consist of conditions and a result. The configured compliance rules are evaluated from top to bottom against conditions and the first match applies. If a rule matches then the templates are assigned. The fact that a rule is matched does not mean that the switch or it's interfaces are evaluated as compliant. It only determines, which template or templates will be used for compliance evaluation. Interface state will be determined based on the compliance template result which will match the interface configuration (if any). If a switch does not match any rule then the switch is considered as non compliant.
If a rule is matched then each interface on the switch is evaluated against the templates in the rule. The templates are evaluated from the first to the last. If a match occurs, then the Template Result is assigned to the interface. Even though the templates can be configured in any order, it is recommended to configure the templates in the order: 1. Non Compliant 2. Part Compliant 3. Compliant.
The following screen shows an example of the Compliance Rules configuration
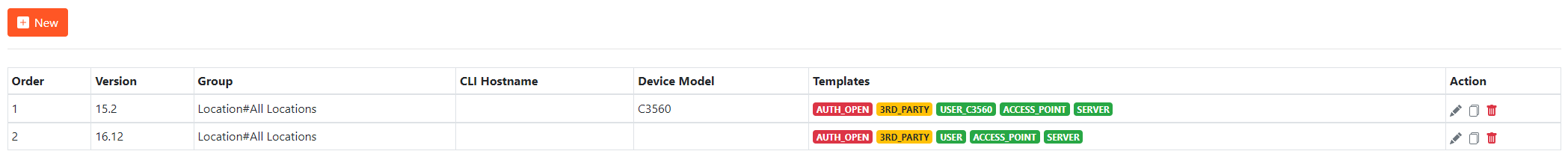
Configuration Guidelines
Every rule can contain the following conditions:
- Version - For example 15.2, 16.9 etc. Version condition is matched against the switch IOS major and minor version is located at the beginning of running configuration.
- Group - For example Location#All Locations#London, Device Type#All Device Types#Cat9200. Refers to ISE groups, the switch is a member of. The value of Location#All Locations is preconfigured as all network devices are members of this group by default but the value can be changed if needed, you can use any network device group (NDG) configured in ISE
- CLI Hostname - Refers to a hostname of a switch (Hostname which is in the switch configuration. Not a device name in ISE configuration)
- Device Model - Refers to the part number of a switch which can be found in
sh versionorsh inventoryoutput
Every condition can have multiple values separated by comma which are evaluated in OR manner. Different conditions are then evaluated in AND manner.
Configuration
- Navigate to Compliance Module -> Compliance Configuration (Page 2)
- Click on the New button
- Fill the Version, Group, CLI Hostname, Device Model and enter comma separated Compliance Templates. Then click Save button

3. Global Setting
The next thing to configure in Compliance Module are Global Settings which affects the behavior of Compliance Module. To configure the Global Setting, navigate to Compliance Module -> Compliance Configuration (Page 3)
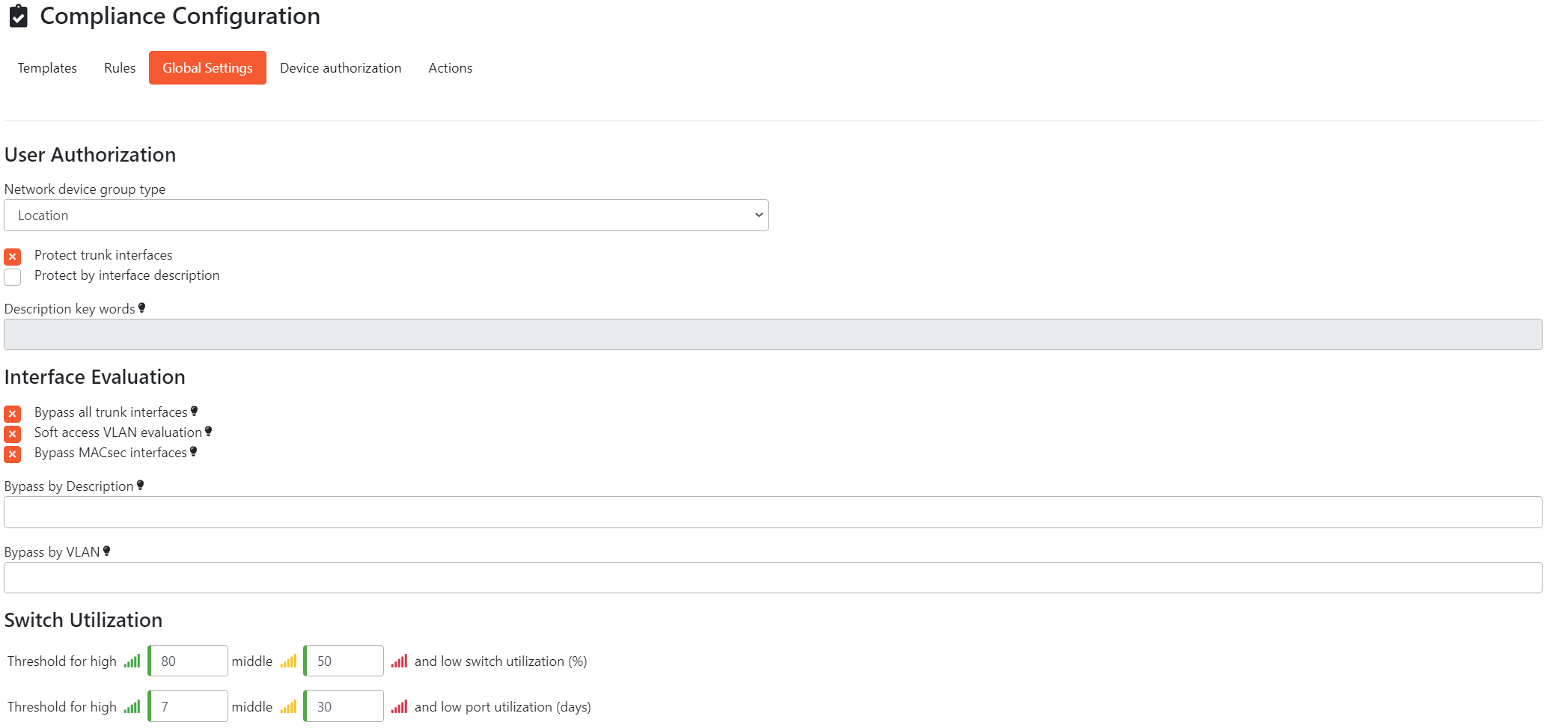
We recommend you to keep options Bypass all trunks, Soft access VLAN evaluation and Bypass MACsec interfaces enabled as we consider it as a best practice.
Settings decription
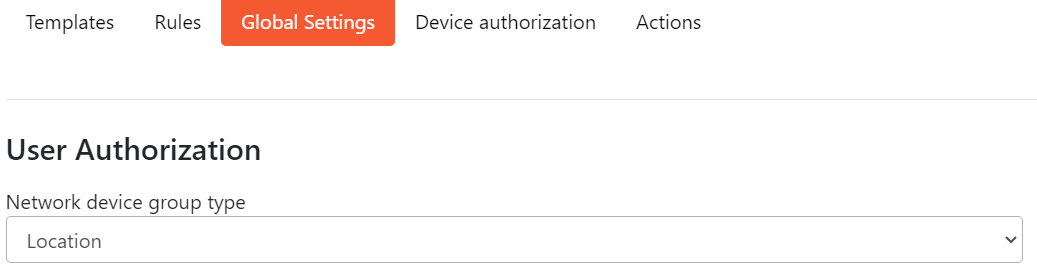
- User Authorization - This configuration is relevant to Device Authorization. It specifies which group from ISE will be used for configuration of authorization rules.
In most cases administrator want to use groups based on location. However, for some usecases other parameters from ISE such as Device Type can be used.
- Protect trunk interfaces - Trunk interfaces will be protected
- Protect by interface description - Interfaces containing the entered keywords will be protected. You can enter comma separated keywords.
Protected interfaces will limit Administrators and Users from sending SSH commands and configurations to interfaces. The User role will not be able to send SSH commands or configure interfaces. The Administrator role will be able to send SSH commands only, but a warning will be displayed.
- Bypass all trunk interfaces - This option will automatically mark all trunk interfaces as bypass. Otherwise only the first trunk interface will be automatically evaluated as Bypass
- Soft access VLAN evaluation - This option will evaluate access ports with incorrect VLAN as Part Compliant
- Bypass MACsec interfaces - If enabled, all MACsec protected interfaces will be automatically evaluated as Bypass
- Bypass by description - If any of specified values is found in the interface description. The interface will be set as Auto Bypass thus exempted from evaluation. The comparison is made in the contains manner and is case insensitive. Enter comma-separated values
- Bypass by VLAN - Enter one or more comma-separated VLAN numbers. If the evaluated interface is configured with any of specified access VLAN numbers. The interface will be set as Auto Bypass thus exempted from evaluation
More details about interface states such as Bypass or Exception can be found later in the documentation.
- Switch Utilization - Administrators have the ability to set thresholds for switch and switchport utilization. This directly impacts the color-coded behavior of the icons in the Device List.
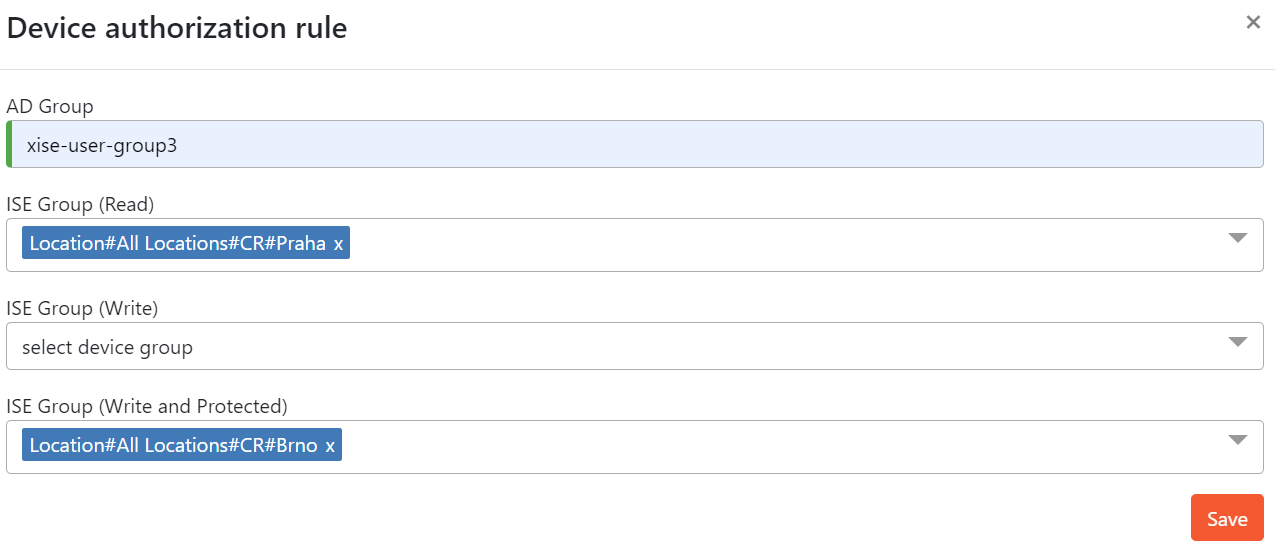
4. Device Authorization
Administrators can configure authorization to network devices based on user's Active Directory group membership. Administrators are able to match devices based on network device groups from ISE (for example location) and grant access to the device only for users who are members of the proper AD group.
The following screen shows an example of the Compliance Rules configuration:
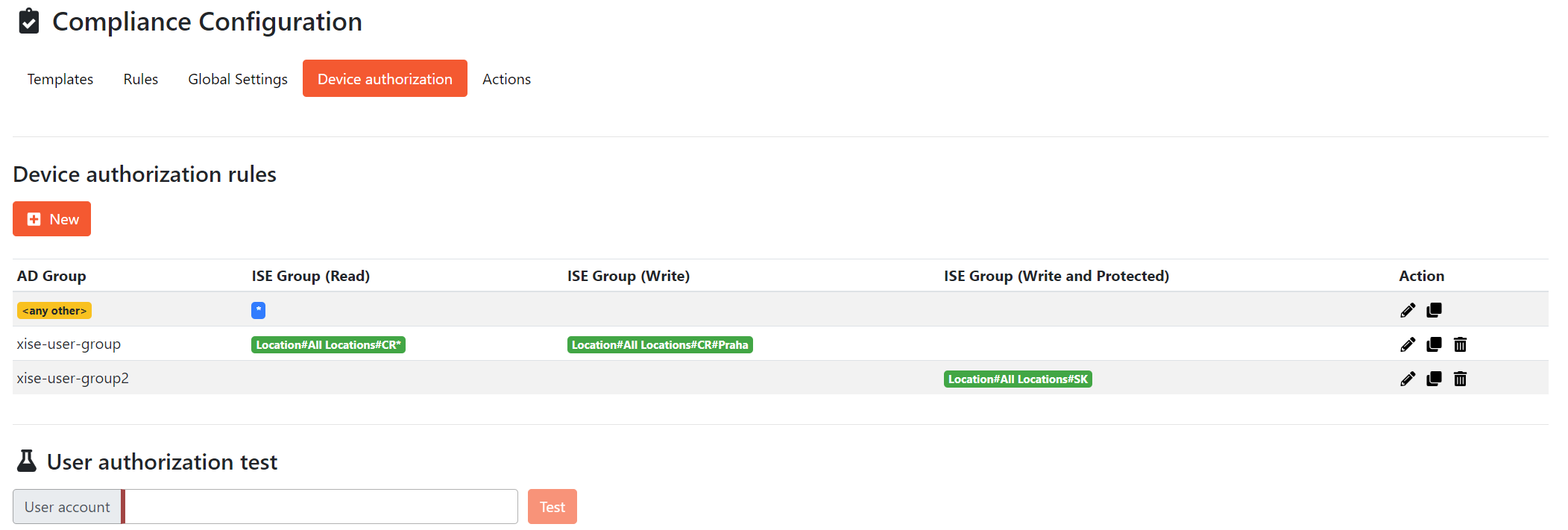
Configuration Guidelines
Every rule can contain the following conditions:
- AD Group - Active Directory group, you want to specify access to network devices
- ISE Group (Read) - Read-only access to the devices from the specified group
- ISE Group (Write) - Write access to the devices from the specified group
- ISE Group (Write and Protected) - Write access (Protected Interfaces included) to the devices from the specified group
There is a default rule that control access for users who haven't been explicitly configured in the subsequent rules. By default, this rule grants read-only access to all network devices.
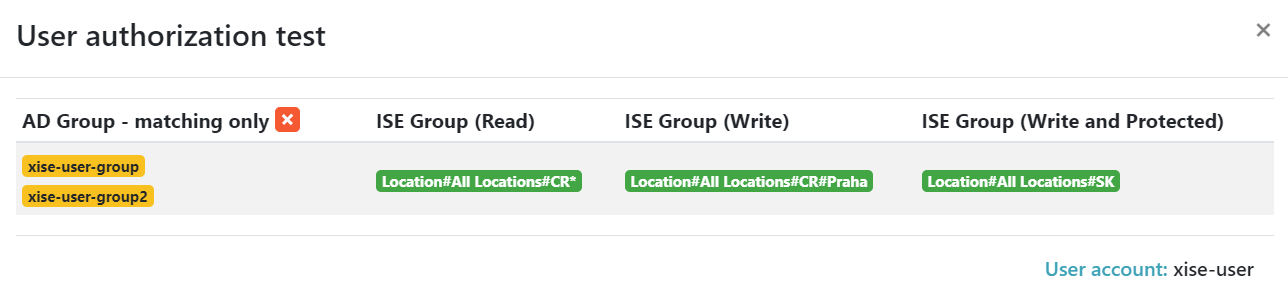
The user authorization test provides the definitive outcome of user rights. This can be particularly useful when a user belongs to multiple Active Directory groups. The final result is a combination of all rules that are applied to the individual user.
Configuration
-
Navigate to Compliance Module -> Compliance Configuration (Page 2)
-
Under the User Authorization select which ISE groups you want to use for Device Authorization
-
Navigate to Compliance Module -> Compliance Configuration (Page 3)
-
Click on the New button
-
Fill the AD Group and choose from the menu correct groups for the level of access you want to grant to the user. Then click Save button
5. Compliance Jobs
Compliance Module consists of two jobs, which are responsible for the Compliance Module runtime.
- Device Synchronization
- Device Evaluation
In the default configuration, the Device Synchronization job is enabled but the Device Evaluation job is disabled. This means that in the Compliance Module is disabled by default.
Device Synchronization
Device synchronization is responsible for synchronization of Network Devices (Network switches) from ISE to XTENDISE. XTENDISE periodically downloads the list of Network Devices configured in ISE and stores it in internal database.
To enable Device Synchronization job, navigate to Compliance Module -> Compliance Configuration (Page 4) and click the Device Sync button.
You can check the job status on the Maintenance page. Device Synchronization job runs every Saturday at 1 a.m. or can be initiated manually.
The compliance module currently supports only Cisco switches thus it only synchronizes switches with the Network Device Profile equals to Cisco and RADIUS configuration in ISE.
Device Evaluation
Device evaluation job is responsible for compliance evaluation of each network device synchronized from ISE. During the evaluation, XTENDISE connects to every switch and evaluates its configuration. This means that every interface in each switch is compared against Compliance Templates and given a result.
To enable Compliance Evaluation job, navigate to Compliance Module -> Compliance Configuration (Page 4) and click the Run Compliance button.
You can check the job status on the Maintenance page. Compliance Evaluation job runs every Sunday at 1 a.m. or can be initiated manually.
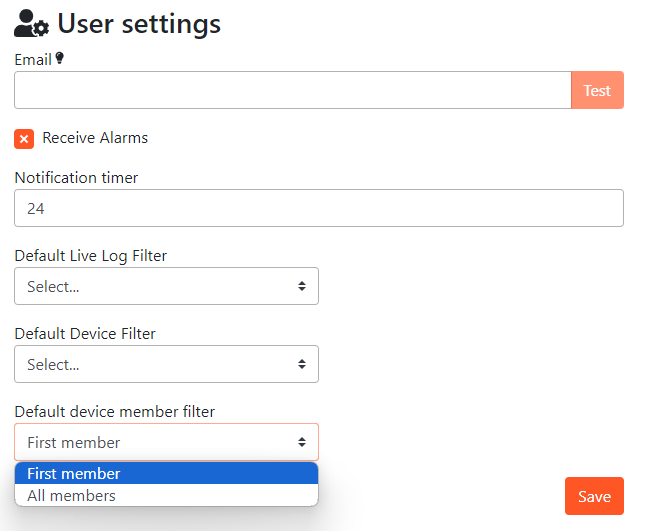
6. User settings
These are user specific configurations.
Device Detail Filtering
XTENDISE user can adjust default behaviour of Device detail by configuring Device detail member filter.
User can choose between two modes:
- First member - only first switch in the stack is shown in the Device detail
- All member - all switches from the stack are shown in the Device detail
Configuration
- Navigate to User Settings -> Default device member filter
- Select prefered option